Is it possible to hack android using image or pdf as a payload?
@Vigneshpvk Thanks for participating in the community. This is a good question. Look at this picture.
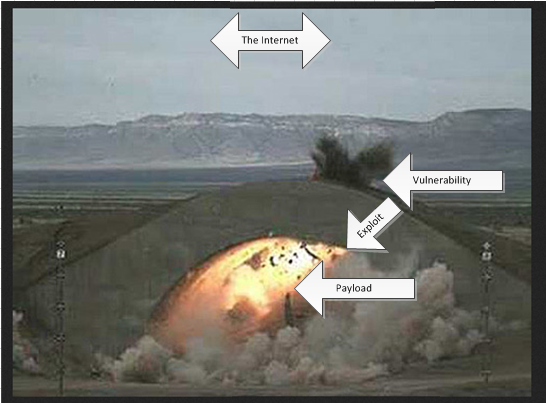
Now click this picture read the info and come ask me again and I will give you the answer you ask for. See you soon.
Yes i have been read it. Now tell it. is practically possible to exploit?
@Vigneshpvk Yes its possible. As an example in MetaSploit we see this in the exploit module use exploit/android/fileformat/adobe_reader_pdf_js_interface
The video you shared is by creating a apk and then social engineer your victim to install it on his/her device. This is not the answer to the question.
Yes it is possible to hack android device without apk payload in one condition that the android device or the android version has got a vulnerability that can be exploited without sending any payload. As we saw in android lollipop version. There existed a vulnerability that can be used to hack a android device running on lollipop just by sending a clean text message.
Then their may be a vulnerability in the android device or you can hack it through link (by just opening. but the session will automatically shut down once the victim close the browser)
Can you tell how to exploit android lolipop version to exploit with clean message
I think you are looking for steganography…
You can upload a script or virus or whatever you want in an image
Thats all i can share:
I think Stenography is used only for sending secret messages to someone. I don’t know whether stenography allows us to remote execute a android by sending virus in image @R4gn4r
Steganography works and to hide viruses/payloads etc.
This method is used to make undetectable exploits etc. and fool the victim easier.
For example someone in the previous year made 2 images and put into them payloads with steganography technique and upload the images on Twitter. And anyone who copied these images were connected with his pc.
I will try this methoid to exploit android remotly. Can you try this method if you get remote execution then tell me. @R4gn4r
If some type of software makes something work(android os in this case) then it can be exploited/hacked.
Nothing is immune and unfortunately no developer writes perfect code.
Anything that can be hacked was my point.
There is always a way.
Sometimes it’s easy sometimes it takes more thought and research.
Yes, There are really lots of ways to hack android just google it .