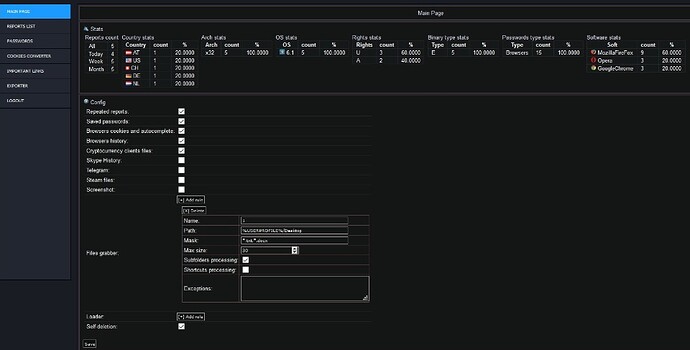
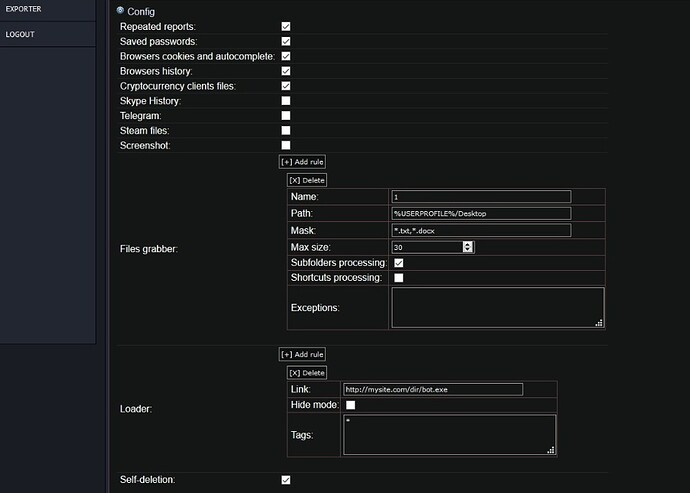
New AZORult 3.4.1 hit the public. Who is the author is unknown, but it feels more stable than grunt 3.3, and the builder will be smaller.
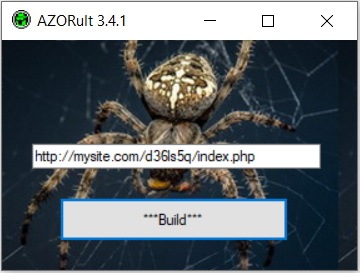
It can be seen that the author does not abandon the work begun. In this builder, you can already hide the admin area further in the site’s folders,and at the root of the site, for example, place a dummy site.
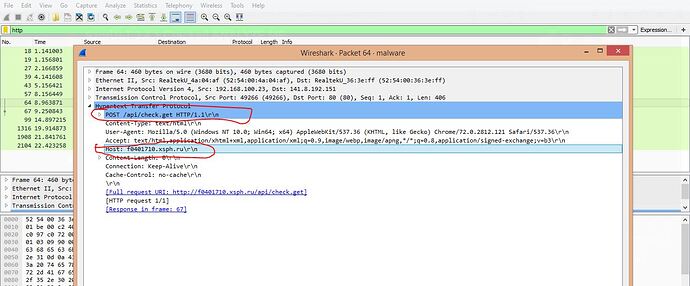
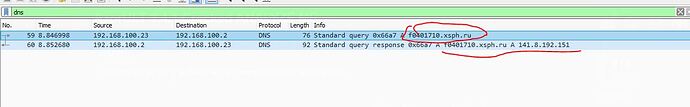
Also now url to admin panel is encrypted and
it cannot be read in the hex editor.
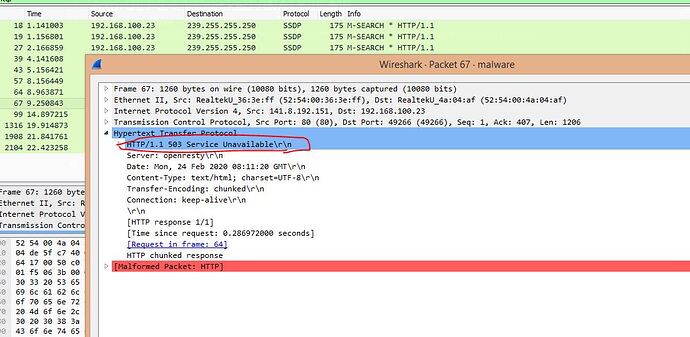
According to the previous version, there were questions about jerks in some cases to the left address.
Probably customers complained and in this version everything is fixed: -
Build knocks exclusively in your admin area.
According to tests, this is so far the best exe azorult builder in the public that I managed to see.
As always, it seems that no glues were found, but to sleep peacefully we launch the software on the virtual machine
What were the changes on the admin panel is not known for certain, but it’s recommended to use that admin panel with it to avoid misunderstandings,
which comes with the kit.
DO NOT DOWNLOAD THIS UNLESS YOU INTEND TO DO MALWARE ANALYSIS ON IT. - https://mega.nz/#!9UIBVabT!wWGZh7sq9COOUqD1Fv-eWuMYrJySwzmpvFhY894GuNU
Pass- AzorULT
According to rumors, this is not the latest version, there is another 3.4.2, it has already added the function of creating a stiller in the form of a dll. But so far no one has laid it out in public.