hey guys, so lately i have been working with alot of MikroTik routers (which generally use the routeros framework) Due to this i made a new program, MkCheck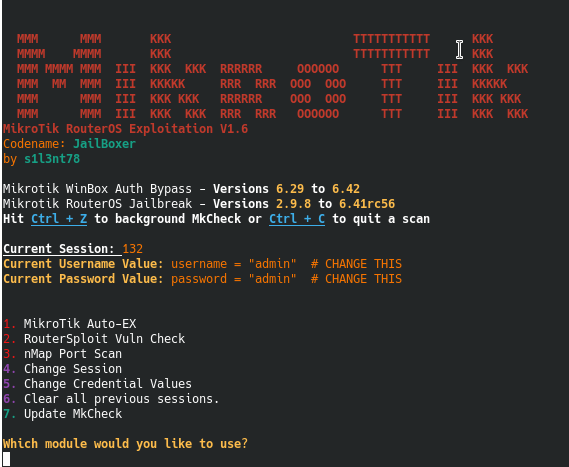
 which allows you to quickly check a list of IP’s to check if port’s 22 and 8291 are open. Then checks (using Routersploit) for Winbox_auth_bypass_cred_disclosure (if found vulnerable dumps the routers http config pages login details), you can then browse to the IP and login to work with that routers configuration. This does not give you the WiFi AP password but that can be found or changed through the config page. Another function pertaining to this particular attack also dumps the WiFi AP names of the checked IP’s. This along with the ability of logging into the config settings allows an attacker a foothold into the network, which can be used to begin exploitaion of machines and servers within the network.
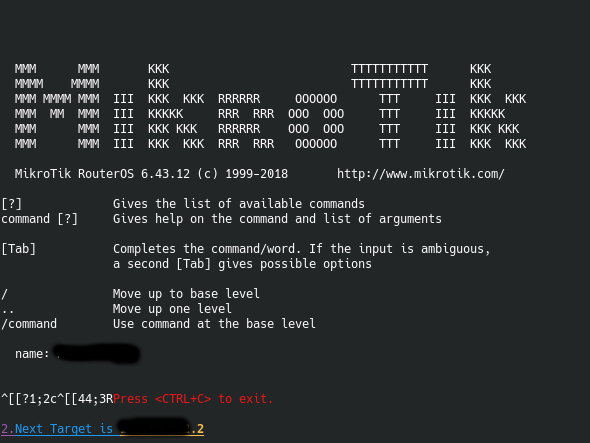
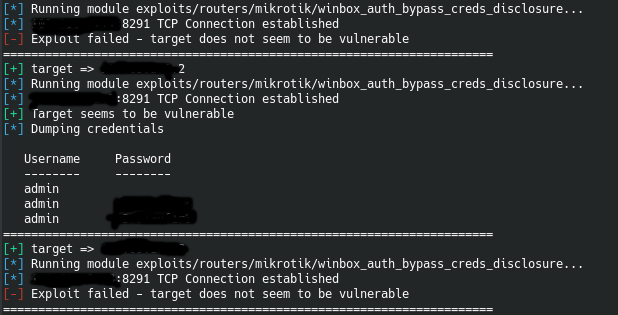
which allows you to quickly check a list of IP’s to check if port’s 22 and 8291 are open. Then checks (using Routersploit) for Winbox_auth_bypass_cred_disclosure (if found vulnerable dumps the routers http config pages login details), you can then browse to the IP and login to work with that routers configuration. This does not give you the WiFi AP password but that can be found or changed through the config page. Another function pertaining to this particular attack also dumps the WiFi AP names of the checked IP’s. This along with the ability of logging into the config settings allows an attacker a foothold into the network, which can be used to begin exploitaion of machines and servers within the network.
Other vulns checked are routeros_jailbreaking and ByTheWay root shell backdoor vulns.
*s1l3nt78
[DISCLAIMER] Do not use this program on a network or router that you do not have explicit permission to do so, or that you do not personally own yourself.