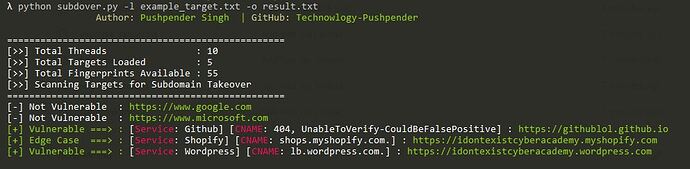
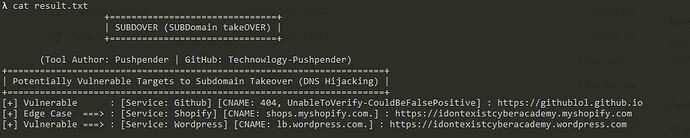
Hello Friends! In This Short Tutorial, I will be showing my own Subdomain Takeover vulnerability scanner tool written in python3.
I Have collected fingerprints from various open source projects such as Aquatone, Subzy, Subjack & SubOver.
Also, I added my own 4-5 fingerprints & corresponding CNAME record in this tool.
So till now it no. 1 tool having largest collection of fingerprints & CNAME record.
I personally tested this tool against many targets in order to decrease the chances of False Positives.
For more detailed info, you can read these section below.
Subdover is a MultiThreaded Subdomain Takeover Vulnerability Scanner Written In Python3, Which has more than 55+ Fingerprints of potentially vulnerable serivces. Uses CNAME record for verfication of findings.
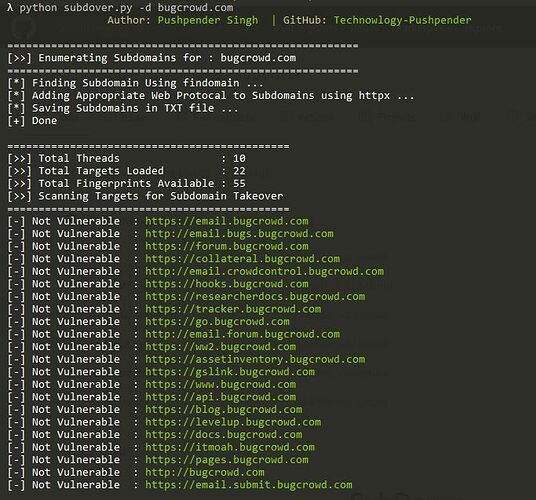
Built-in Subdomain Enumeration Feature & Auto HTTP prober [Uses Open Source Tool for Subdomain Enum & HTTP probing i.e. findomain & httpx]
Features
- More than 55+ Fingerprints of potentially vulnerable services
- Uses CNAME record for verification of findings
- Built-in Subdomain Enumeration Method [Used findomain for Subdomain Enum]
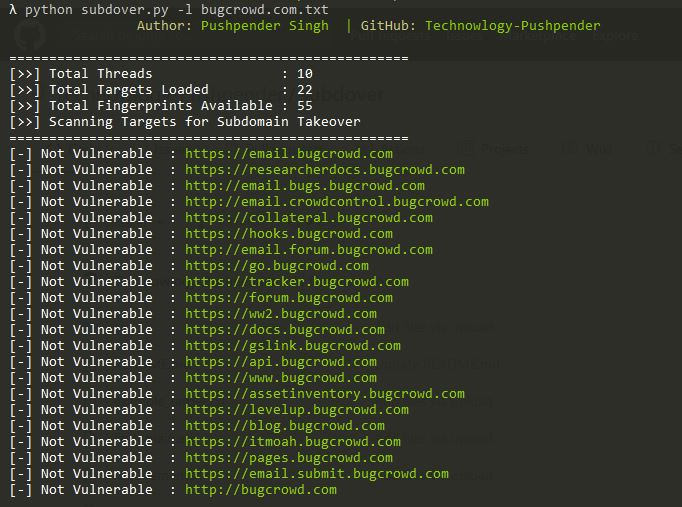
- Can Scan targets from subdomain list
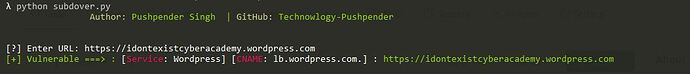
- Can Test Single Target for Subdomain Takeover
- MultiThread, Extermely Fast Scanner [Default Threads: 10]
- You can choose number of threads
- You can save result in TXT file
- Extremely Clean Output
- OS Independent [Can be used on any OS which supports Python3]
Tested On
Prerequisite
- Python 3.X
- Few External Modules
How To Use in Linux
# Navigate to the /opt directory (optional)
$ cd /opt/
# Clone this repository
$ git clone https://github.com/Technowlogy-Pushpender/subdover.git
# Navigate to subdover folder
$ cd subdover
# Installing dependencies
$ apt-get update && apt-get install python3-pip
$ pip3 install -r requirements.txt
# If you want to enumerate subdomain using this script only, then you have to install findomain in your OS
$ # Check out this URL for Installtion Guide: https://github.com/Edu4rdSHL/findomain
# Giving Executable Permission & Checking Help Menu
$ chmod +x subdover.py
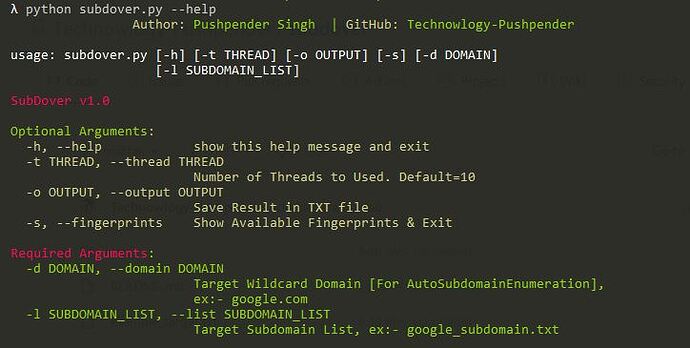
$ python3 subdover.py --help
# Testing Single Target [Running Without Giving Parameter]
$ python3 subdover.py
# Enumerating Subdomain & Testing them for Subdomain Takeover
$ python3 subdover.py -d target.com
# Testing targets for Subdomain Takeover from subdomain list
$ python3 subdover.py --list example_target.txt
# Changing Number of Threads
$ python3 subdover.py --thread 30 -d target.com
# Saving Result
$ python3 subdover.py -d target.com -o result.txt
# Show Fingerprints & Exit
$ python3 subdover.py -s
How To Use in Windows
# Download this project as zip
# Navigate to subdover folder
$ cd subdover
# Installing dependencies
$ python -m pip install -r requirements.txt
# Checking Help Menu
$ python subdover.py --help
# Testing Single Target [Running Without Giving Parameter]
$ python subdover.py
# Enumerating Subdomain & Testing them for Subdomain Takeover
$ python subdover.py -d target.com
# Testing targets for Subdomain Takeover from subdomain list
$ python subdover.py --list example_target.txt
# Changing Number of Threads
$ python subdover.py --thread 30 -d target.com
# Saving Result
$ python subdover.py -d target.com -o result.txt
# Show Fingerprints & Exit
$ python subdover.py -s
Available Arguments
- Optional Arguments
| Short Hand | Full Hand | Description |
|---|---|---|
| -h | –help | show this help message and exit |
| -t | –thread | Number of Threads to Used. Default=10 |
| -o | –output | Save Result in TXT file |
| -s | –fingerprints | Show Available Fingerprints & Exit |
- Required Arguments
| Short Hand | Full Hand | Description |
|---|---|---|
| -d | –domain | Target Wildcard Domain [For AutoSubdomainEnumeration], ex:- google.com |
| -l | –list | Target Subdomain List, ex:- google_subdomain.txt |
Available Fingerprints & CNAMES of potentially vulnerable servies
| No. | Service Name |
|---|---|
| 1. | Acquia |
| 2. | Activecampaign |
| 3. | AfterShip |
| 4. | Aha |
| 5. | Apigee |
| 6. | AWS/S3 |
| 7. | Bigcartel |
| 8. | Bitbucket |
| 9. | Brightcove |
| 10. | CampaignMonitor |
| 11. | Cargo |
| 12. | CargoCollective |
| 13. | Cloudfront |
| 14. | Desk |
| 15. | Fastly |
| 16. | Feedpress |
| 17. | Freshdesk |
| 18. | GetResponse |
| 19. | Ghost |
| 20. | Github |
| 21. | Help Juice |
| 22. | Help Scout |
| 23. | Heroku |
| 24. | Instapage |
| 25. | InterCom |
| 26. | JetBrains |
| 27. | Kajabi |
| 28. | Mashery |
| 29. | MicrosoftAzure |
| 30. | Pantheon |
| 31. | Pingdom |
| 32. | Proposify |
| 33. | Readme.io |
| 34. | Shopify |
| 35. | SimpleBooklet |
| 36. | Smartling |
| 37. | Smugmug |
| 38. | StatusPage |
| 39. | Strikingly |
| 40. | Surge.sh |
| 41. | Surveygizmo |
| 42. | Tave |
| 43. | Teamwork |
| 44. | Thinkific |
| 45. | Tictail |
| 46. | Tilda |
| 47. | Tumblr |
| 48. | Unbounce |
| 49. | UptimeRobot |
| 50. | UserVoice |
| 51. | Vend |
| 52. | WebFlow |
| 53. | WishPond |
| 54. | Wordpress |
| 55. | Zendesk |