A successful Red Team engagement begins with clearly defining the goals/objectives of the engagement with the client.
The Red Team is then tasked with planning and orchestrating the engagement based on the pre-defined goals/objectives.
It is important to note that Red Team engagement does not focus on the search for vulnerabilities, instead, they target security operations as a whole.
The results of a Red Team engagement should highlight the Blue Team’s ability to detect and defend against attacks and where improvements can be made.
Red Team engagements should also simulate/emulate new TTPs for the Blue Team to learn how to detect and defend against.
A successful Red Team engagement requires a structured methodological approach, especially when simulating/emulating an adversary.
It is therefore recommended to use an appropriate Red Team methodology/framework as a basis on which to plan, structure, and orchestrate your campaign.
Frequently utilized Red Team frameworks/methodologies include:
- Cyber Kill Chain
- MITRE ATT&CK Framework
RED TEAM FRAMEWORKS & METHODOLOGIES
- Cyber Kill Chain (Lockheed Martin): Cyber Kill Chain® | Lockheed Martin
- MITRE ATT&CK - https://attack.mitre.org/
- Unified Cyber Kill Chain - https://www.unifiedkillchain.com/
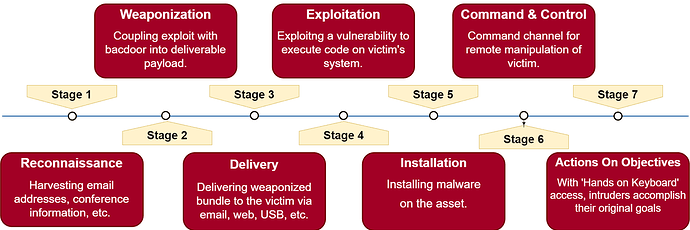
CYBER KILL CHAIN
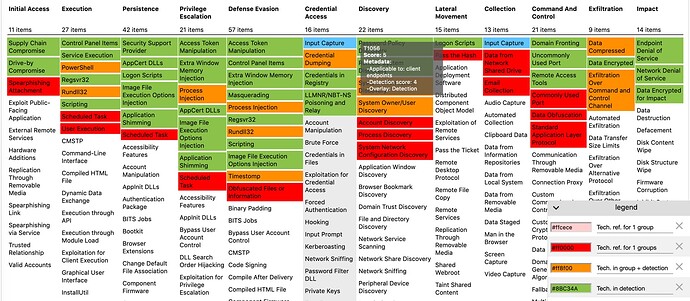
MITRE ATT&CK FRAMEWORK
ATT&CK VS CYBER KILL CHAIN
| MITRE ATT&CK | Cyber Kill Chain |
|---|---|
| Recon | Recon |
| Resource Development | Weaponization |
| Initial Access | Delivery |
| Execution | Exploitation |
| Persistence | Installation |
| PrivEsc | C2 |
| Defense Evasion | Actions On Objectives |
| Credential Access | |
| Discovery | |
| Lateral Movement | |
| Collection | |
| Command and Control | |
| Exfiltration | |
| Impact |
This post is also available in the form of a PDF:
Red Ream Frameworks & Methodologies.pdf (1.7 MB)